Can I Refuse a Voluntary Cleanup Request From the Dtsc in Ca
Resolving Issues Starting a CA due to an Offline CRL

Resolving bug when attempting to starting time a certificate authority due to an offline CRL.
- The Issue
- The Workaround
- The Cause of an Offline CRL
- How To Fix It
- Conclusion
I recently wrote a couple of articles on setting up and Root Certification Authority and a Subordinate Certification Potency as a basic cheat sheet for setting up and Enterprise PKI. One configuration item that is less well understood and oft the crusade of major headaches with certificate government, is the Certificate Revocation List (CRL). An Offline CRL can bring down your PKI and other services that rely on it.
The Result
You might find your document say-so, in this case, a subordinate certificate authority that is not started, possibly after a server reboot. Attempting to kickoff the CA, results in this message:
The revocation part was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)
Which looks like this:
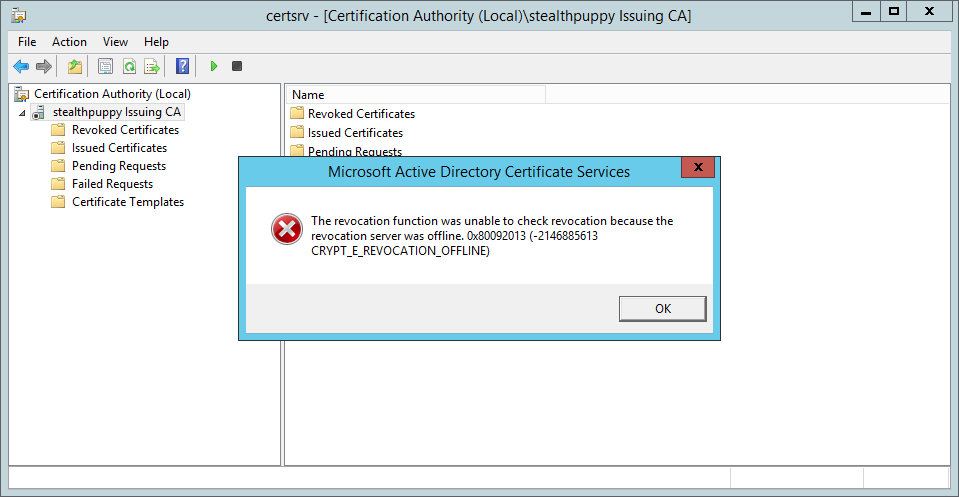
In the Awarding log on the subordinate CA, I can run into event id 100 from source CertificationAuthority:
Active Directory Certificate Services did non start: Could not load or verify the current CA certificate. stealthpuppy Issuing CA The revocation function was unable to cheque revocation considering the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
Every bit well as, event id 48 from the same source, CertificationAuthority:
Revocation condition for a certificate in the chain for CA certificate 0 for stealthpuppy Issuing CA could not be verified because a server is currently unavailable. The revocation function was unable to check revocation considering the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
Certificate 0 is the subordinate CA's certificate, issued by the offline Root CA.
In addition (past starting the CA with a workaround) I can run into a number of failed document requests with the aforementioned Offline CRL result:
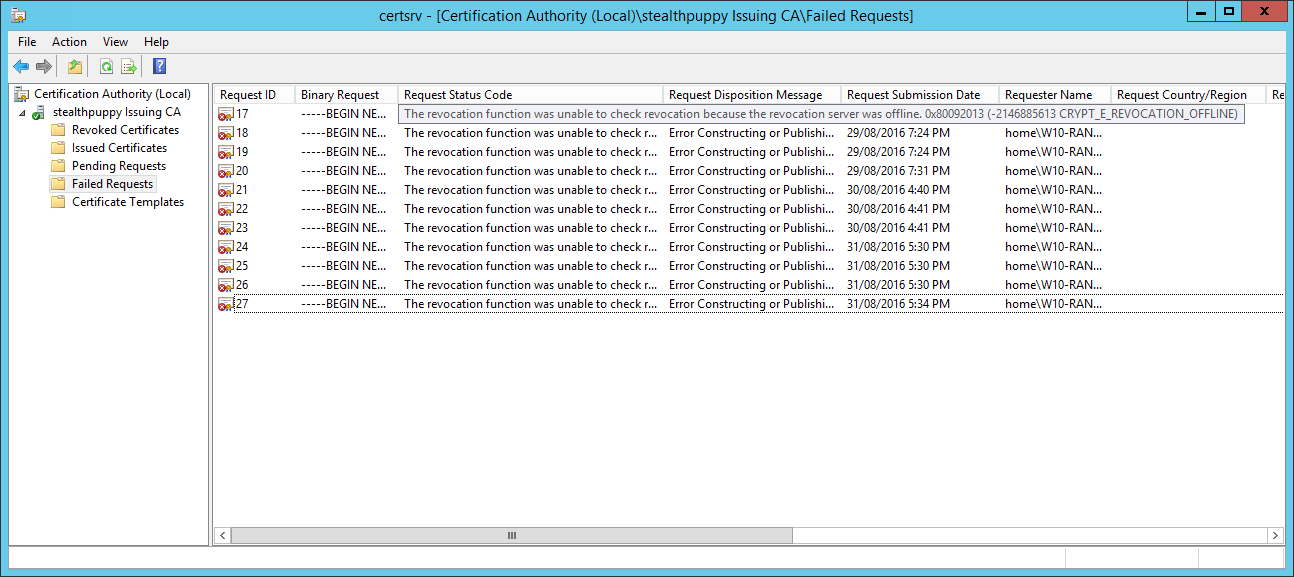
In this instance, I knew that my CRL was online - information technology'due south the same server as the subordinate CA and I had configured both the offline Root CA and the Subordinate CA for the same CRL distribution indicate.
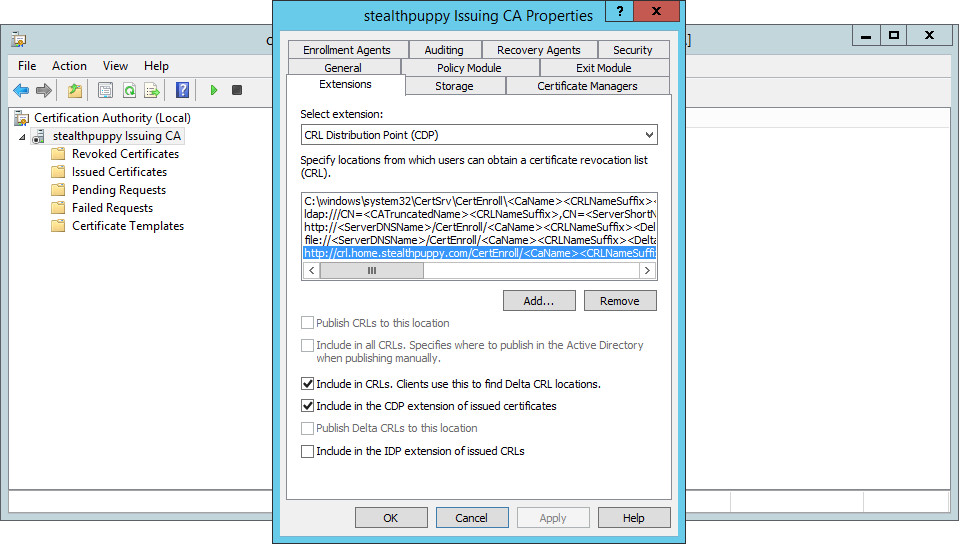
CRL distribution point on the Subordinate CA
The Workaround
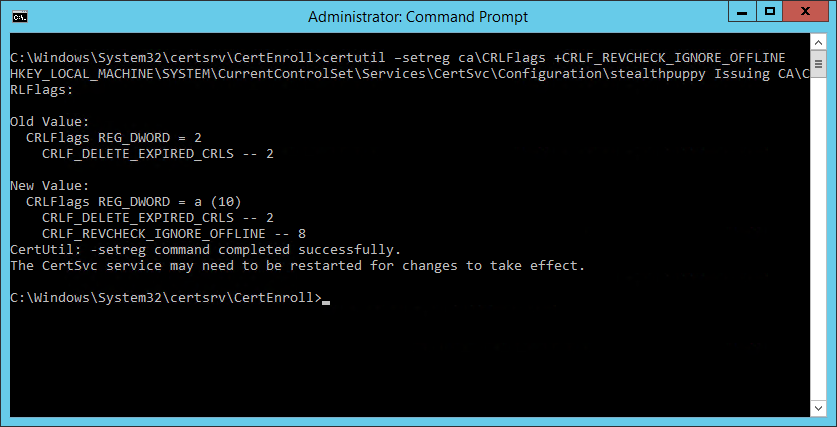
Of course, you probably desire to get the CA up and running equally speedily as possible. The easy way to do that is to disable CRL checking with the following control on the CA server:
certutil – setreg ca\CRLFlags + CRLF_REVCHECK_IGNORE_OFFLINE Run this from an elevated command prompt and you should now exist able to get-go the CA and become on with the business organisation of troubleshooting.
The Cause of an Offline CRL
My CRL was online every bit it is available in Active Directory (for domain joined machines) and via HTTP at crl.dwelling house.stealthpuppy.com, an alias of the subordinate CA. I've tested that I can think the CRL by putting the HTTP path into a browser and I'm prompted to download a file.
http://crl.home.stealthpuppy.com/CertEnroll/stealthpuppy Issuing CA.crl http://crl.home.stealthpuppy.com/CertEnroll/stealthpuppy Offline Root CA.crl Through having spent some time recently with setting upward an Enterprise PKI in my lab and for a project, I've come to know the control line tool certutil.exe. This tool is bachelor in all versions of Windows and should exist the first tool to employ to troubleshoot and manage certificates and certificate authorities on Windows.
Certutil tin can be used to perform many functions, one of which is to verify a CRL. I know the path to the CRL file because I tin view the CRLs on the file system (in C:\Windows\System32\certsrv\CertEnroll) and I've previously configured CRLs for both CAs.
To verify the CRL, apply the -URL switch with the HTTP (or LDAP) path to the CRL:
certutil -URL "http://crl.home.stealthpuppy.com/CertEnroll/stealthpuppy Issuing CA.crl" This will display the URL Retrieval Tool that shows that the CRLs are able to exist contacted and show a condition of OK.
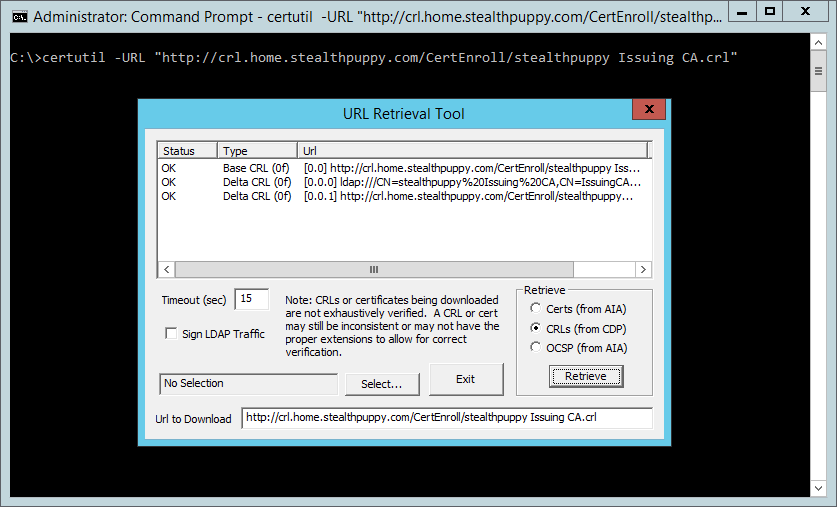
All the same, if we load a target certificate, in this example, the subordinate CA's cert, we tin can start to see why we have an upshot with the CRL.
Select the document for the subordinate CA that has been previously exported to the file organization (in C:\Windows\System32\certsrv\CertEnroll) - click Select, open the certificate and click Retrieve again. This time, nosotros can encounter a new line that shows that the base CRL for the subordinate CA'southward certificate is Expired.
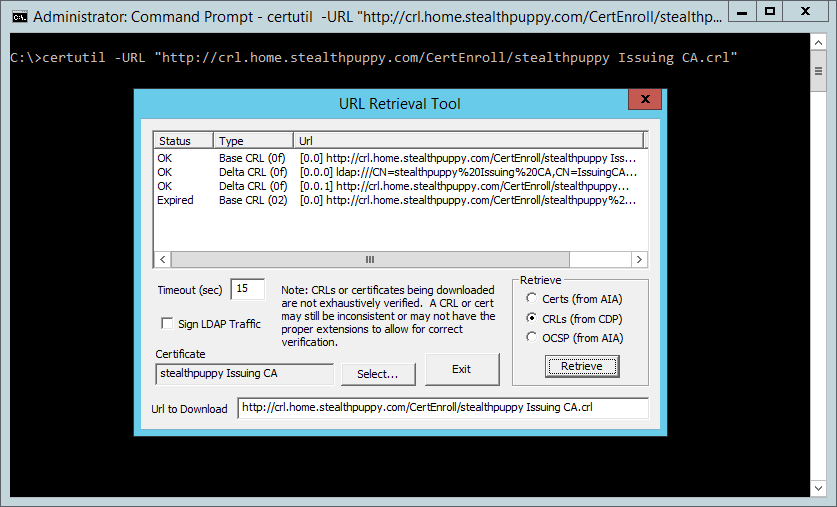
The CRL for the subordinate CA's document will come from the root CA, so we'll need to check that CRL. Open up the CRL file (C:\windows\system32\certsrv\CertEnroll\stealthpuppy Offline Root CA.crl) - double-click or right-click and Open up. Here we tin see the CRL information, including the next publishing time (Next CRL Publish).
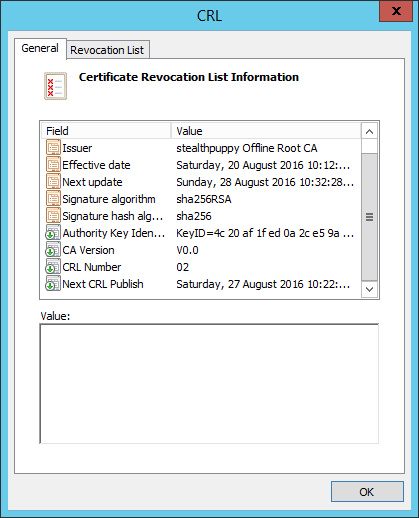
At the fourth dimension of troubleshooting, this date was in the past and because the Root CA is offline and the CRL is hosted on a different server (the subordinate CA), this detail CRL will never receive an update. And then, when the subordinate CA has rebooted, information technology has checked the Root CA'southward CRL and plant information technology expired. Hence the certification potency service won't start.
How To Fix It
Now we know why the certification authority service won't start and an understanding of why the CRL is offline, fifty-fifty if the diction doesn't match the symptoms. If the error bulletin had told me the CRL had expired instead of being offline, I might have saved some troubleshooting time. We now know that we need to re-publish the CRL from the Root CA.
Start the offline Root CA, log into information technology and open the Certification Dominance panel. We will first want to ensure that the CRL publication interval is extended and then that we don't run into the same problem in the near future. Open the properties of the Revoked Certificates node to view and ready the publication interval. The default interval is 1 calendar week, obviously too oft for an offline Root CA.
Instead, set this value to something suitable for the environs you have installed the CA into. Remember that y'all'll need to boot the Root CA and publish a new CRL before the stop of this interval, otherwise, you'll have exactly the same issue.
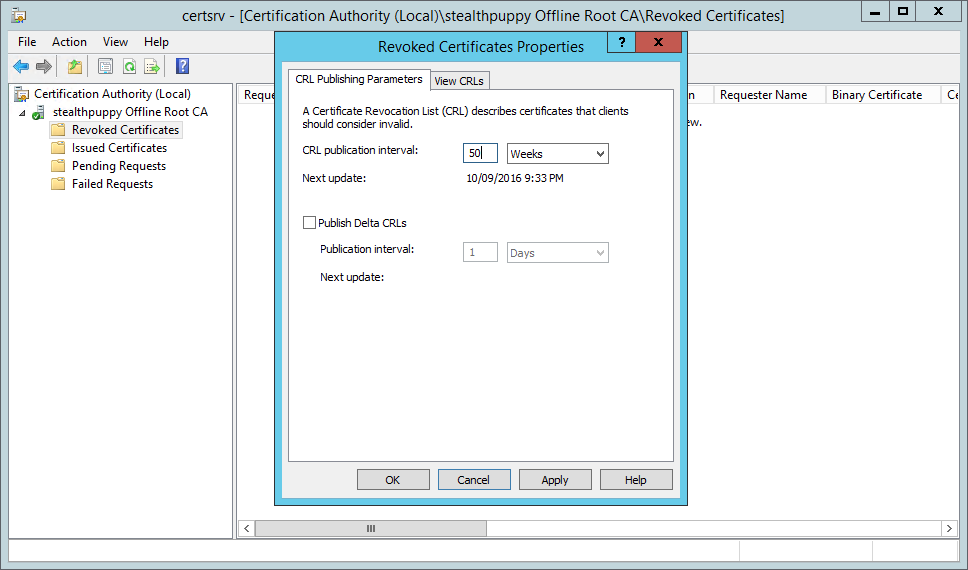
Now publish a new CRL - right-click the Revoked Certificates node and click All Tasks / Publish.
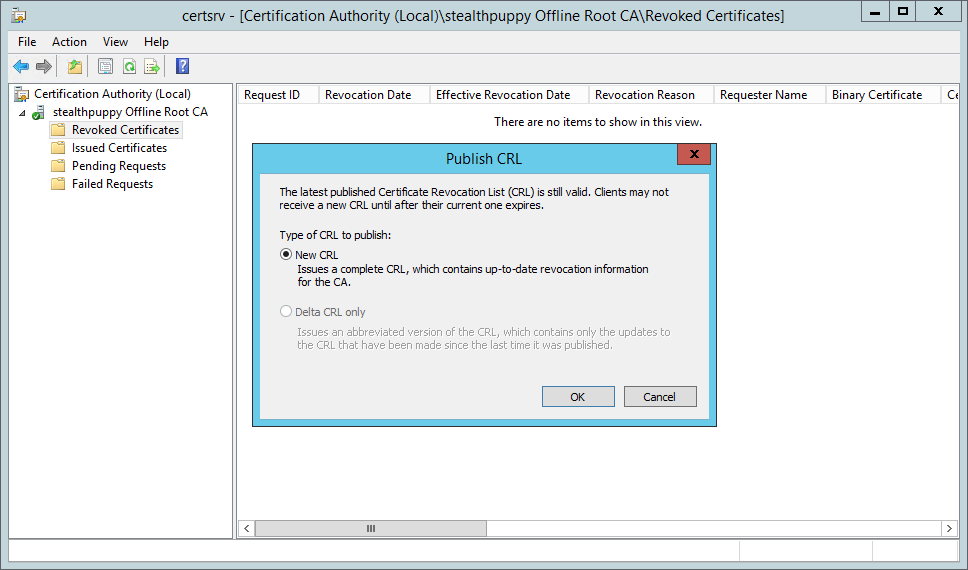
Copy the updated CRL (from C:\Windows\System32\certsrv\CertEnroll past default) from the Root CA to the CRL distribution betoken and overwrite the existing CRL file (C:\Windows\System32\certsrv\CertEnroll again on my subordinate CA).
Now if we again utilize certutil.exe to verify the CRL, it comes up roses:
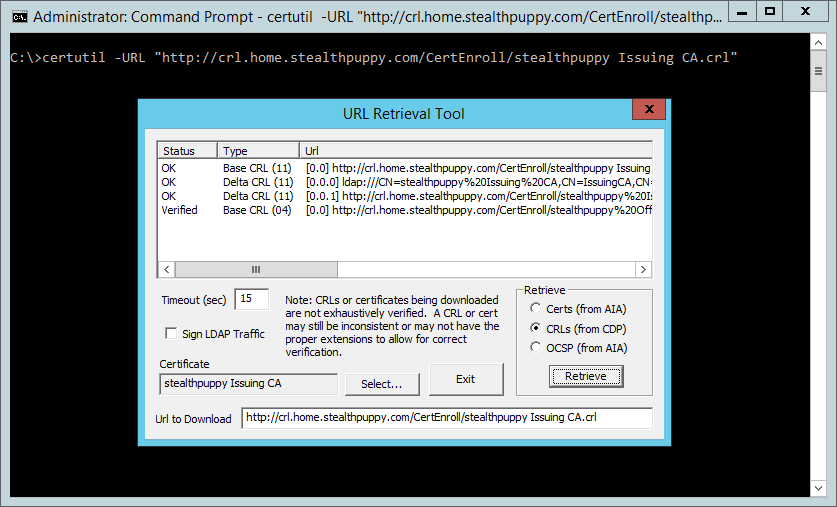
Viewing the verified CRL with certutil.exe
To ensure that the subordinate CA's certification authority service will start, re-enable CRL checking:
certutil – setreg ca\CRLFlags -CRLF_REVCHECK_IGNORE_OFFLINE If yous have re-published the CRL from the Root CA correctly, the service should starting time and y'all can then shut downwardly the Root CA. Then open up Outlook and put a reminder in the agenda for a week before the CRL expires again.
Conclusion
I've had this issue with an Offline CRL a few times now and not really understood what the outcome is until I took the fourth dimension to troubleshoot the issue properly. I don't spend that much time with an enterprise PKI and it'due south easy to underestimate the complexity of setting up AD Certificate Services correctly.
This aforementioned issue has too caused me headaches with a Network Device Enrollment Service (NDES) deployment for issuing certificates to devices via Intune. The expired CRL has caused the NDES service to not commencement and the events logged do not mention in whatsoever way, an expired CRL.
Source: https://stealthpuppy.com/resolving-issues-starting-ca-offline-crl/
0 Response to "Can I Refuse a Voluntary Cleanup Request From the Dtsc in Ca"
Post a Comment